Did you ever need to script ‘setting-file/folder-permissions’ or making a deployment or install script ? Or did you ever screwed-up the NTFS permissions on the C:\Windows folder (including all the subfolders) ?
If so, you’d better read on;
Microsoft finally came with a solution which stops all the horror of automaticly setting-NTFS permissions, including the slow and buggy CACLS variants.
First, i show the timeline and history of the Microsoft tools for setting permissions;
CACLS.EXE was invented for Windows NT4.0 and used for Windows 2000 to set NTFS permissions to files. This tool was not powerfull and only had a few options for setting very-basic NTFS permissions.
XCACLS.EXE (within the Windows 2000 Resource Kit or Microsoft Windows 2003 Support Tools) was made to provide more options for Windows 2000 and up. However, there were some bugs where NTFS permissions were incorrectly ordered and would corrupt the permissions of the file/folder.
XCACLS.VBS was Microsoft’s follow-up and was a rewritten (VBS) version of XCACLS.EXE without the bugs. However, it was so slow! Unfortunately this was the only way to set file permissions on a correct/stable way on Windows 2000/2003/XP.
Now, a few years later, Microsoft finally introduced the new powerfull ICACLS.EXE.
It is included in Windows Server 2003 SP2, Windows Vista and Windows Server 2008. This tool is much faster in setting permissions, it has functionality to backup the permissions of a complete set of files/folders to a single file. You can restore them with the same tool, which is even faster than setting all permissions independently.
UPDATE: After 2 days and nights working and scripting with ICACLS, i saw some limitations; One of them is that you can’t break inheritance.
For example:
When your E:\ drive has Full-Control for the Administrator user with inheritance, you can not use ICACLS to set E:\test\abc\ with just Read permissions for the Administrator user. (see my detailed example at EE)
I tried using “icacls E:\test\abc\ /grant:r Administrator:(OI)(CI)(NP)(R)” but this just adds the read permissions while maintaining the Full-Control permissions. Using icacls with “/remove Administrator” didn’t work either.
The function is possible with the XCACLS.VBS command: “cscript.exe xcacls.vbs E:\test\abc /I COPY|REMOVE|ENABLE“.
You can also use the Windows GUI (see screenshots):
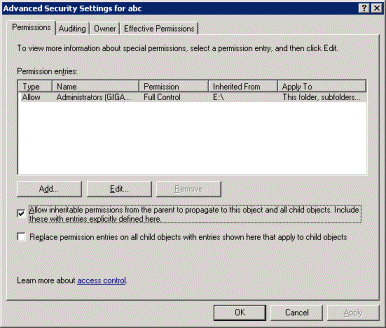
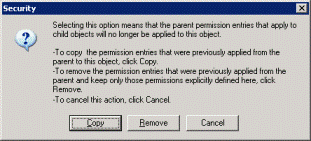
Below is the usage, syntax and some examples of ICACLS, post your own more-complex examples ! (MSDN command reference)
C:\Windows\System32\icacls.exe
ICACLS name /save aclfile [/T] [/C]
store the the acls for the all matching names into aclfile
for later use with /restore.
ICACLS directory [/substitute SidOld SidNew [...]]
/restore aclfile [/C]
applies the stored acls to files in directory.
ICACLS name /setowner user [/T] [/C]
changes the owner of all matching names.
ICACLS name /findsid Sid [/T] [/C]
finds all matching names that contain an ACL explicitly
mentioning Sid.
ICACLS name /verify [/T] [/C]
finds all files whose ACL is not in canonical form or whose
lengths are inconsistent with ACE counts.
ICACLS name /resize [/T] [/C] [/L]
changes incorrect recorded lengths of ACLs to true lengths
ICACLS name /reset [/T] [/C]
replaces acls with default inherited acls for all matching
files
ICACLS name [/grant[:r] Sid:perm[...]]
[/deny Sid:perm [...]]
[/remove[:g|:d]] Sid[...]] [/T] [/C]
/grant[:r] Sid:perm grants the specified user access rights.
With :r, the permissions replace any previouly granted
explicit permissions.
Without :r, the permissions are added to any previously
granted explicit permissions.
/deny Sid:perm explicitly denies the specified user access
rights.
An explicit deny ACE is added for the stated permissions
and the same permissions in any explicit grant are
removed.
/remove[:[g|d]] Sid removes all occurrences of Sid in the
acl.
With :g, it removes all occurrences of granted rights to
that Sid.
With :d, it removes all occurrences of denied rights to
that Sid.
Note:
Sids may be in either numerical or friendly name form. If a
numerical form is given, affix a * to the start of the SID.
/T indicates that this operation is performed on all
matching files/directories below the directories
specified in the name.
/C indicates that this operation will continue on all
file errors.
Error messages will still be displayed.
ICACLS preserves the canonical ordering of ACE entries:
Explicit denials
Explicit grants
Inherited denials
Inherited grants
perm is a permission mask and can be specified in one of two
forms:
a sequence of simple rights:
F - full access
M - modify access
RX - read and execute access
R - read-only access
W - write-only access
a comma-separated list in parenthesis of specific
rights:
D - delete
RC - read control
WDAC - write DAC
WO - write owner
S - synchronize
AS - access system security
MA - maximum allowed
GR - generic read
GW - generic write
GE - generic execute
GA - generic all
RD - read data/list directory
WD - write data/add file
AD - append data/add subdirectory
REA - read extended attributes
WEA - write extended attributes
X - execute/traverse
DC - delete child
RA - read attributes
WA - write attributes
inheritance rights may precede either form and are
applied only to directories:
(OI) - object inherit
(CI) - container inherit
(IO) - inherit only
(NP) - don't propagate inherit
Examples:
icacls c:\windows\* /save AclFile /T
- Will save the ACLs for all files under c:\windows
and its subdirectories to AclFile.
icacls c:\windows\ /restore AclFile
- Will restore the Acls for every file within
AclFile that exists in c:\windows and its
subdirectories
icacls file /grant Administrator:(D,WDAC)
- Will grant the user Administrator Delete and Write DAC
permissions to file
icacls file /grant *S-1-1-0:(D,WDAC)
- Will grant the user defined by sid S-1-1-0 Delete and
Write DAC permissions to file
If you want to know more about the (OI), (CI), (IO) and (NP) (inheritance) flags, see this Microsoft KB article.
I recently found this document about ICACLS, see page 8 – 10.
A good alternative to ICACLS is “fileacl” (free, 3rd party). It’s lightning fast and even an (ASP) COM interface is available! An older version is even downloadable from the MS site, so i think they even like it ;)
[…] Finally, ICACLS Valhalla!. Roel Broersma, 2007. […]
Nice post Roel.
One other limitation with xcaclc.vbs is that it doesn’t work when setting permissions on folders under a DFS structure. You need to access the folder structure via the actual share instead. Another reason for changing over to icacls…
Cheers,
Jeremy.
Update : There currently is a “bug” in iCACLS.exe supplied in SP2 for Windows Server 2003:
– This issue arises when attempting to use the /setowner switch, which returns an “Access is denyed.” message.
Currently, (as of May 2008) MS has a limited release hotfix to resolve this issue wiht iCACLS.exe on Windows Server 2003. (See KB Article 947870)
– Note that this bug is NOT present on the iCACLS.exe with Vista SP1 or Windows Server 2008.